FRAME 5
The challenge and reply authentication system uses the test element and an authenticator.
Another system, which is referred to as transmission authentication, is used ONLY when
authentication becomes necessary for a station and it is either not possible or not operationally
desirable for the receiving station or stations to reply; for example, when the net control station
(NCS) directs or imposes radio or listening silence on a net. The transmission authentication
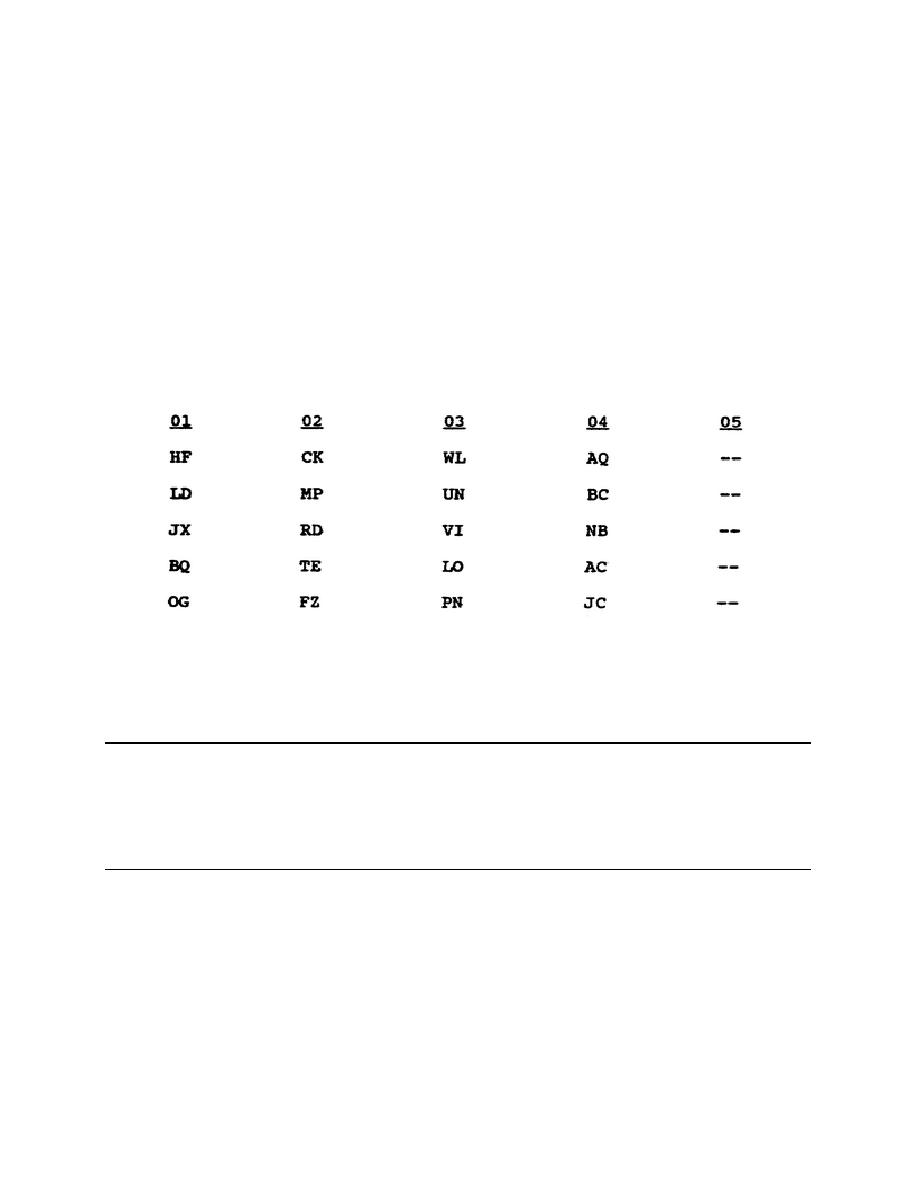
table consists of numbered columns of digraphs. The columns are numbered to facilitate
allocation of digraphs to selected stations to avoid reuse of digraphs during a given cryptoperiod.
When it becomes necessary to use transmission authentication, the first or next unused digraph is
selected.
TRANSMISSION AUTHENTICATION TABLE
For voice transmission, the authentication digraph is transmitted phonetically
immediately preceding the ending proword, prefixed by the phase "Authentication is
__________ __________." For example, if the digraph is HF, use the phrase "Authentication is
Hotel Foxtrot."
2-29. All stations in the communications net must line through each used digraph to prevent its
reuse. Any attempted reuse of a digraph in the same communications net must be considered as
an attempted intrusion. The reuse of any digraph in a communications net is prevented since
each station in the net must __________ __________ each __________ that is used.
(2-29. Answer: line through, digraph)
2-11
SS0652



 Previous Page
Previous Page
