(2) Reliability.
The effectiveness
and quality of information depends on its
reliability. Proper signal support procedures,
well-maintained equipment, and well-trained
soldiers achieve reliability.
(3) Redundancy is achieved by
duplicating facilities, equipment, and/or
information of critical systems, providing
alternate routes for all vital information, and
providing automatic real-time outing and the
capability for quick reconstitution within the
network.
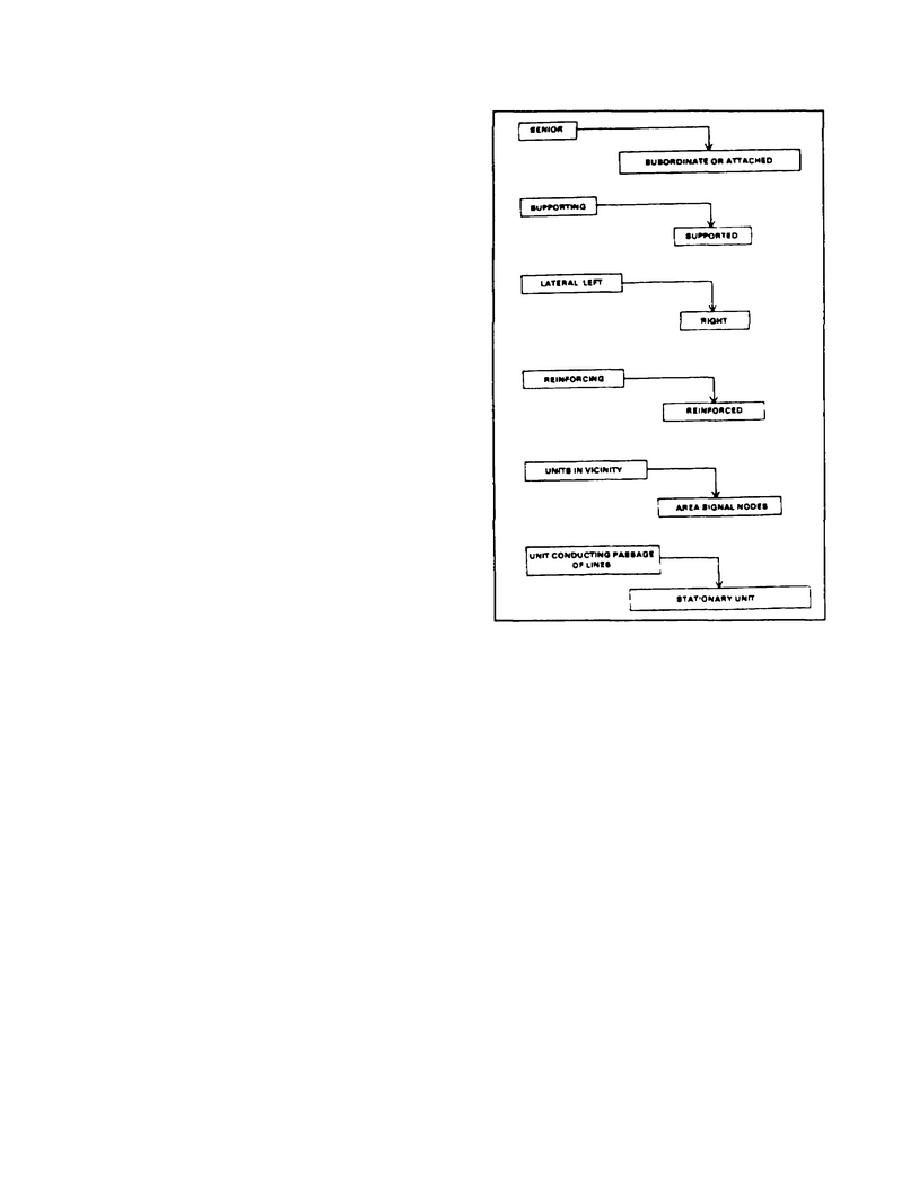
(4) Connectivity
is
established
higher to lower and left so right (see Figure 1-
3). Signal support provides fully connected
paths for the effective transfer of information.
b. Security maintains the integrity of
the force. It supports the AirLand Battle tenets
of initiative, agility, and synchronization. The
subordinate elements of security are:
(1) Information
security
is
preventing unauthorized persons from gaining
information from signal support systems. It is
Figure 1-3.
achieved by use of COMSEC and physical
Connectivity relationships
security means.
(2) Physical security is achieved by the use of cover, concealment, camouflage, and
obscurants to protect signal support systems and sites from attack.
(3) Dispersion is the geographical separation of information systems to optimize
survivability of soldiers and systems.
(4) Deception is achieved by saturating the battle area with a system of nodes that prevent
association with any unit, function, or echelon, using electronically indistinguishable emission signature
or simulating U.S. communications nodes at false locations to confuse or mislead the enemy on our
information systems.
1-9
SS0118



 Previous Page
Previous Page
